Today’s technology has accumulated with large-scale data produced by devices. All of them share massive volume of information, so organizations need an effective tool for control, monitoring and fighting against potential threat. Security Information and Event Management (SIEM) Systems play a key role at organizations in monitoring both real-time events and a mountain of long-term data to detect anomalous patterns of utilization and alert organizations whenever needed. The underlying principle of SIEM system is that the relevant information about the security of an enterprise is produced in diverse sources, and the data is correlated and viewed from one central location.
In simple words, SIEM is a combination of two different types of technologies:
– SIM (Security Information Management) that focuses on log collection and report generation
and
– SEM (Security Event Manager) that analyses events in real-time using event correlation and alerting mechanism
In details, SIM segment mainly emphasizes on the analysis of historical data intending to improve the long-term storage performance and efficiency of information security infrastructures. On the contrary, SEM area emphasizes on the aggregation of data into a manageable amount of information with the aid of which security incidents can be dealt with immediately.
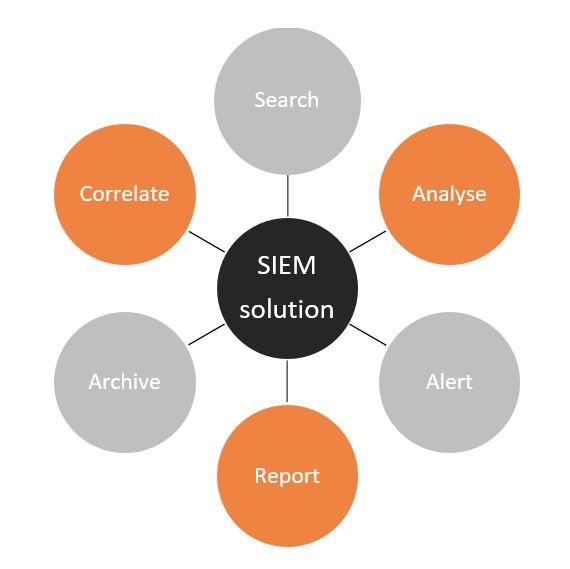
SIEM Technology provides network security intelligence and real-time monitoring for network, devices, systems and applications. SIEM systems collect logs and other security-related documentation for analysis. Most of them work by deploying multiple collection agents in a hierarchical manner to gather security-related events from end-user devices, servers, network equipment – and even specialised security equipment like firewalls, antivirus or intrusion prevention systems. The collectors forward events to a centralised management console, which performs inspections and flags anomalies.
If your company is planning to choose a SIEM solution, there are a few things you should take into account about it:
#1. User Activity Monitoring
– SIEM solutions should have Out-of-the-box user activity monitoring and audit reporting feature
– Ensuring that the SIEM solution gives the “Complete audit trail”; Know which user performed the action, what was the result of the action, on what server it happened and from where the action was triggered.
#2. File Integrity Monitoring
– File Integrity Monitoring helps security professionals in monitoring business critical files and folders
– Ensure that the SIEM solution tracks and reports on all changes such as when files and folders are created, accessed, viewed, deleted, modified, renamed and much more.
– The SIEM solution should also send real-time alerts when unauthorised users access files and folders
#3. Log Forensics
– SIEM solutions should allow users to track down an intruder or the event activity using log search capability
– The log search capability should be very user-friendly, allowing IT administrators to search through the raw log data quickly
#4. Real Time Event Correlation
– Real-time event correlation is all about proactively dealing with threats. Correlation boosts network security by processing millions of events simultaneously to detect anomalous events on the network.
– Custom rule and alert-builder is a must for every SIEM solution.
#5. Log Retention
– SIEM solutions should automatically archive all log data from systems, devices and applications to a centralized repository.
– Ease of retrieving and analysing archived log data
#6. IT Compliance reports
– IT compliance is the core of every SIEM solution
– Ensure that the SIEM solution has out-of-the-box regulatory compliance reports such as SOX, HIPAA, etc.
– SIEM solutions should also have the capability to customise and build new compliance reports to comply with future regulatory acts
#7. Dashboards
– Dashboards drive SIEM solutions and help IT administrators take timely action and make the right decisions during network anomalies.
– Security data must be presented in a very user-friendly manner.
– The dashboard must be fully customisable so that IT administrators can configure the security information they wish to see.
Most enterprises find SIEM necessary because of several factors: Rise in data breaches due to external threats, attackers are smart and traditional security tools just don’t suffice, managing increasing volumes of log from multiple sources and meeting stringent compliance requirements. The business benefits of SIEM solutions are numerous, but the most essential ones relate to real-time monitoring (for operational efficiency and IT security purposes), cost saving, compliance, reporting and rapid ROI.
For more information about other PATECCO solutions, check in the new e-guide:

